
Friedrich-Alexander-Universität Erlangen
Lehrstuhl für Mustererkennung
Martensstraße 3
91058 Erlangen

The goal of blind image forensics is to assess authenticity and origin of digital images without an embedded security scheme. Within this field, three directions can be distinguished to reach this goal.
The research in our group focuses on the second and third branch. Recent results include
Group members in this project: ![]() Christian Riess,
Christian Riess, ![]() Elli Angelopoulou
Elli Angelopoulou


Johnson and Farid enriched image forensics with a method for estimating the lighting direction. From the 2-D contours of an object, the direction and distribution of incident light can be estimated. When we experimented with that method, we noticed that the physics-based constraints impose relatively strict constraints on the method's applicability on images in the wild. In this work, we aim to relax one of the constraints, namely the requirement that the object contour has to be selected on the same material. In our method, we allow for piecewise constant materials along the contour by incorporating an albedo correction term into the equations. The datasets for evaluation can be downloaded ![]() here.
here.
 |
 |
We investigate the algorithms for estimating the illuminant color as a potential cue to expose spliced images. One particular situation of interest are spliced pictures containing multiple faces. We apply different illuminant color estimators specifically to face regions in an image, which adds the prior that the underlying material (skin) should be more homogeneous than in the unconstrained case. Our results indicate that fully automated classification of spliced images of faces is possible. Have a look at the ![]() project page. Code for creating the illuminant maps is available!
project page. Code for creating the illuminant maps is available!
 |
 |
A large number of methods for Copy-Move Forgery Detection (CMFD) have been proposed. In this paper, we conduct a large-scale evaluation on a newly created benchmark. Our results show that keypoint-based detectors have a clear advantage in the computational complexity. A number of block-based features, although relatively expensive to compute, offer in many cases a higher accuracy when it comes to detecting details of the copied region. Have a look at the ![]() project page. Code and data are available!
project page. Code and data are available!
 |
 |
 |
We present a pattern recognition approach to exploit the so-called JPEG Ghost phenomenon for detecting manipulated images. Our fully automated algorithm requires the computation of only six features. It yields highly competitive detection rates on image regions as small as 8x8 or 16x16 pixels. Have a look at the ![]() project page. Code is available!
project page. Code is available!
 |
 |
Copy-Move Forgery Detection has recently advanced towards the detection of rotated and scaled copies of an image region. Some feature sets exhibit very promising detection results. However, the filtering of feature matches in a rotation/scaling scenario suffered so far from a robust, scalable approach. In our paper "On Rotation Invariance in Copy-Move Forgery Detection", ![]() we propose the Same Affine Transform Selection (SATS) as a rotation and scale invariant extension of the popular same shift vector approach. Code is available!
we propose the Same Affine Transform Selection (SATS) as a rotation and scale invariant extension of the popular same shift vector approach. Code is available!
 |
 |
We present a common pipeline for copy-move forgery detection. This formalization allows us to compare the most discriminating properties of various presented methods, their features. We perform an evaluation of ten different feature sets on a part of our benchmark database. Experiments show that the Fourier-Mellin descriptors perform outstandingly when a region is directly copied. When the copied region is additionally rotated or scaled, is PCA and DCT features were the most robust choice.
 |
 |
We present a ![]() dataset and software for large-scale evaluations of tampering artifact detection methods. The dataset consists of 48 different images together with separate tampered image parts. With use of the software, the images and the tampered parts can be freely combined, thus creating data for various realistic tampering scenarios. For instance, Gaussian and salt+pepper noise can be added, tampered parts can be scaled and rotated, as well as JPEG recompressed. We believe that it is about time for a publicly available realistic dataset for the evaluation of methods for tampering artifacts detection, especially copy-move forgery detection.
dataset and software for large-scale evaluations of tampering artifact detection methods. The dataset consists of 48 different images together with separate tampered image parts. With use of the software, the images and the tampered parts can be freely combined, thus creating data for various realistic tampering scenarios. For instance, Gaussian and salt+pepper noise can be added, tampered parts can be scaled and rotated, as well as JPEG recompressed. We believe that it is about time for a publicly available realistic dataset for the evaluation of methods for tampering artifacts detection, especially copy-move forgery detection.
 |
 |
We present a method for the assessment of illumination color consistency in a scene. We extended a physics-based method for illumination color estimation. The presented method can be locally applied on real-world images, such that the consistency of the obtained estimates can be assessed. Taking the fact under consideration that current illuminant estimation methods are highly error-prone, we purposefully decided for a physics-based method. Thus, a human observer is able to judge the validity of the estimates. We further suggest a simple tool, what we call the distance map, for simplified visualization and interpretation of the results. Code for creating the illuminant maps is available on the ![]() project page.
project page.
 |
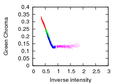 |
We are examining physical properties of a consistent scene. Our particular interest lies in properties of the scene illumination. ![]() In our work, we examined how to adapt illumination estimation algorithms as a cue for semantic image analysis. Most important, we focused on physics-based illumination estimation algorithms, in order to make errors in the estimation explicable. We adapted an illumination estimation method by Tan et al. Most real-world scenes consist of a mixture of specular and diffuse pixels. On such images, our algorithm yields robust results in almost real-time.
In our work, we examined how to adapt illumination estimation algorithms as a cue for semantic image analysis. Most important, we focused on physics-based illumination estimation algorithms, in order to make errors in the estimation explicable. We adapted an illumination estimation method by Tan et al. Most real-world scenes consist of a mixture of specular and diffuse pixels. On such images, our algorithm yields robust results in almost real-time.